Implementing TOTP Authentication Into Your Infrastructure

We have previously covered how to add Time-based One-time Password Algorithm (TOTP) on your mobile device. Now we can implement SSH access with TOTP. It is more secure to use public key authentication, and disable any password and challenge-based authentication for SSH. However, there are times when you have to have access to your server but you don’t have your public keys with you. In this case, we’ll need to allow root level login and secure it with a time-based passcode.
Make sure to sync your server’s clock and start ntpd :
# killall -9 ntpd && ntpdate -b -v 0.pool.ntp.org && service ntpd start
Now we’ll need to install git, pam-devel, and fetch the libpam code:
# yum –y install git pam-devel # git clone https://code.google.com/p/google-authenticator/ /root/ga Cloning into '/root/ga'... remote: Counting objects: 1048, done. remote: Finding sources: 100% (1048/1048), done. remote: Total 1048 (delta 504) Receiving objects: 100% (1048/1048), 2.27 MiB | 1.09 MiB/s, done. Resolving deltas: 100% (504/504), done. # cd /root/ga/libpam && make && make install
After all is done, you’ll have two files installed: /lib64/security/pam_google_authenticator.so and /usr/local/bin/google-authenticator
Modify /etc/pam.d/sshd and add the following line as the first entry:
auth required pam_google_authenticator.so
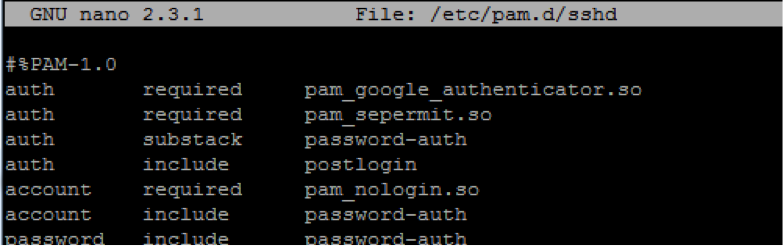
Add the necessary modifications to SSH config and restart the daemon:
PermitRootLogin yes
PasswordAuthentication yes
ChallengeResponseAuthentication yes
Now run google-authenticator and generate your securitykey:
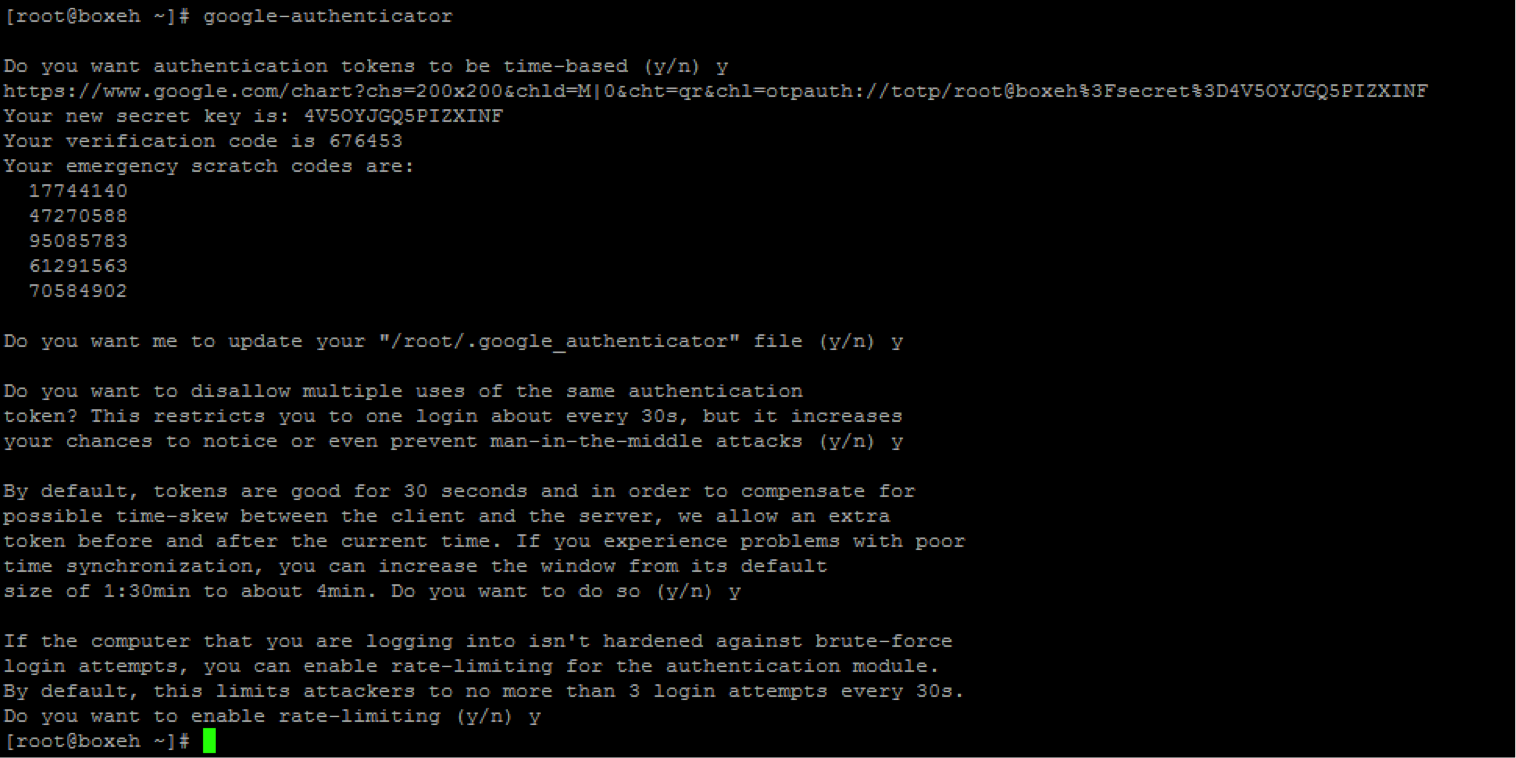
You can add the QR code to your mobile device from link above:

As you can see the secretkey that was generated is “4V5OYJGQ5PIZXINF”. To get a real-time passcode you can use the following Python code:
import hmac, base64, struct, hashlib, time
def get_hotp_token(secret, intervals_no):
key = base64.b32decode(secret, True)
msg = struct.pack(">Q", intervals_no)
h = hmac.new(key, msg, hashlib.sha1).digest()
o = ord(h[19]) & 15
h = (struct.unpack(">I", h[o:o+4])[0] & 0x7fffffff) % 1000000
return h
def get_totp_token(secret):
return get_hotp_token(secret, intervals_no=int(time.time())//30)
my_secret = ‘4V5OYJGQ5PIZXINF’
my_token = get_totp_token(my_secret)
print my_token
You can either use your mobile phone (Android, iOS, Blackberry), or a standalone application to generate the passcodes:
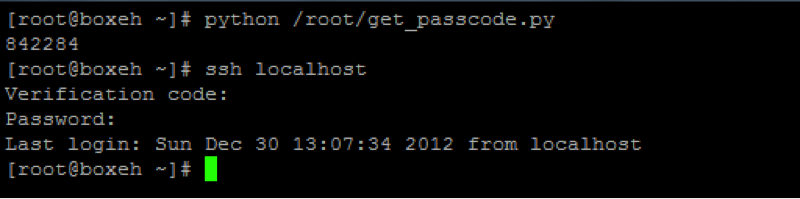
If you entered an incorrect TOTP passcode but still got the correct password, the system would not let you logon, and generate an error in /var/log/secure :
sshd(pam_google_authenticator)[23225]: Invalid verification code
It is worth mentioning that you could migrate the /root/.google_authenticator file to all of your servers and use the same passcode. The file contains the secretkey and emergency scratch off codes that should be written down somewhere safely:
# cat /root/.google_authenticator 4V5OYJGQ5PIZXINF " RATE_LIMIT 3 30 1356890982 1356891010 " WINDOW_SIZE 17 " DISALLOW_REUSE 45229700 " TOTP_AUTH 17744140 47270588 95085783 61291563 70584902
If you ended up using one of the scratch off keys, the file will be automatically updated on the server where you used it. For example, if you used “17744140” to login, the PAM module would delete that key and it would not be re-usable:
# cat /root/.google_authenticator 4V5OYJGQ5PIZXINF " RATE_LIMIT 3 30 1356891395 " WINDOW_SIZE 17 " DISALLOW_REUSE 45229700 " TOTP_AUTH 47270588 95085783 61291563 70584902
You can also add your own scratch off key to the list, but keeping the list short is a good security practice.
Now that you have enabled challenge response authentication, you would need to modify your SFTP settings to “interactive” if you are using an SFTP client like FileZilla.
You will be prompted for the verification code upon connection:
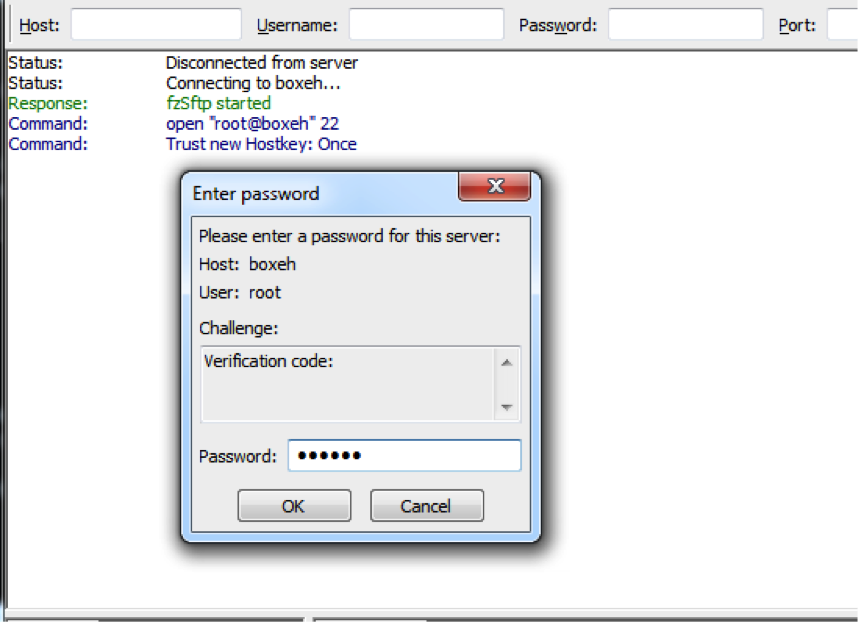
After entering verification code and password, the system will let you login:
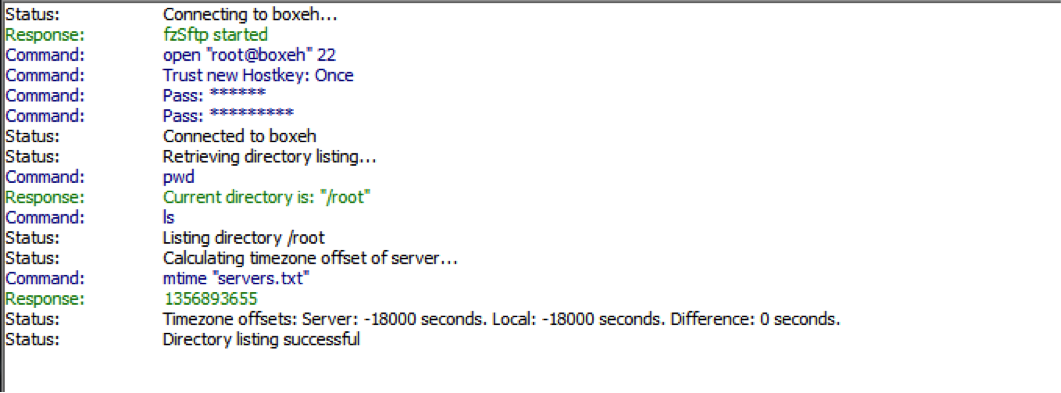
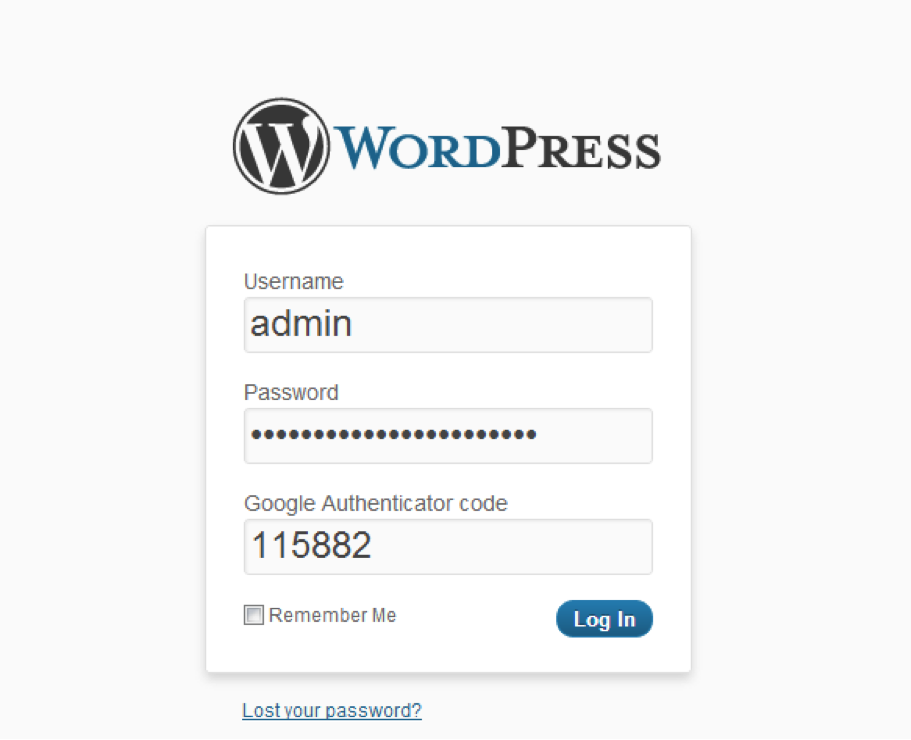
WordPress with TOTP Authentication
Now that you have secure access to your files and command shell, we can also secure access to your WordPress administrative area.
Make sure to sync the clock on the webserver and your device where you’ll be generating the TOTP code.
# killall -9 ntpd && ntpdate -b -v 0.pool.ntp.org && service ntpd start
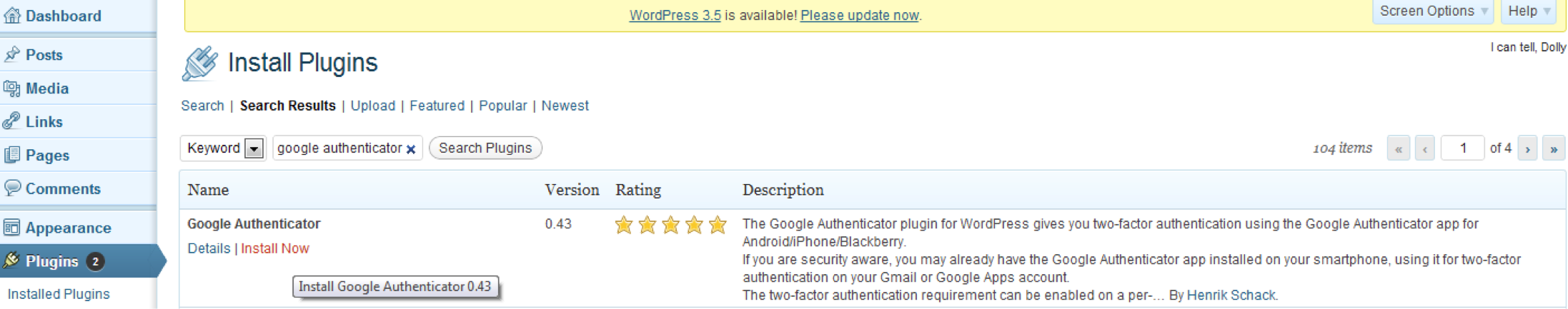
The plugin can be downloaded from http://downloads.wordpress.org/plugin/google-authenticator.0.43.zip or installed directly from WP Plugins menu:
Simply search for ‘google authenticator’ and install it directly:
Activate the plugin and navigate to Users -> Your Profile:
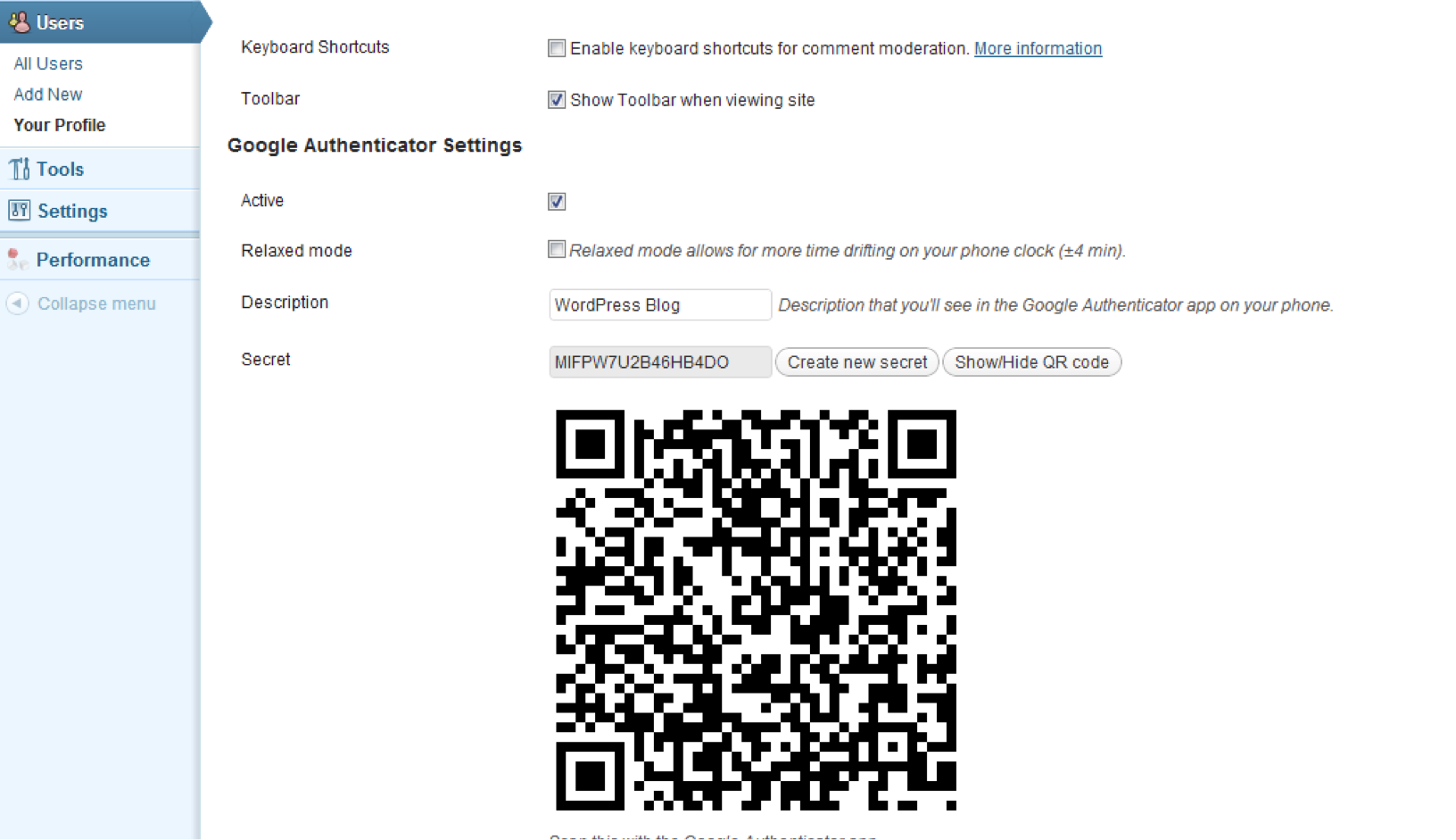
Make sure to generate your QR code and add it on your phone or desktop device :
Check “Active” box, and if your server does not have a reliable time syncing, check ‘Relaxed mode’.
To finalize changes, click “Update Profile” on the bottom, and you are done.
Now your WordPress Admin area is more secure :